After testing 400,000 apps for high-risk security issues, the following data was collected.
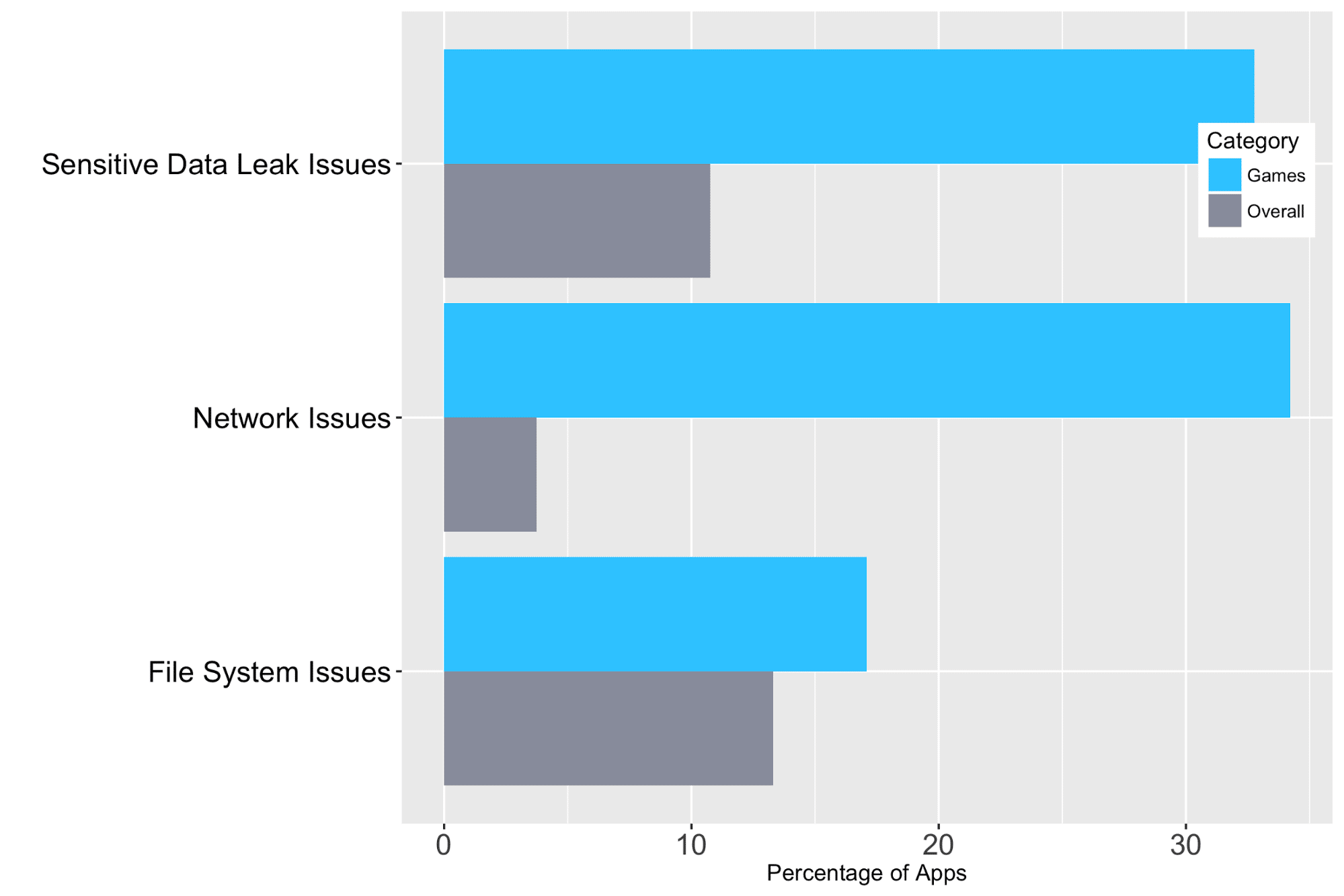
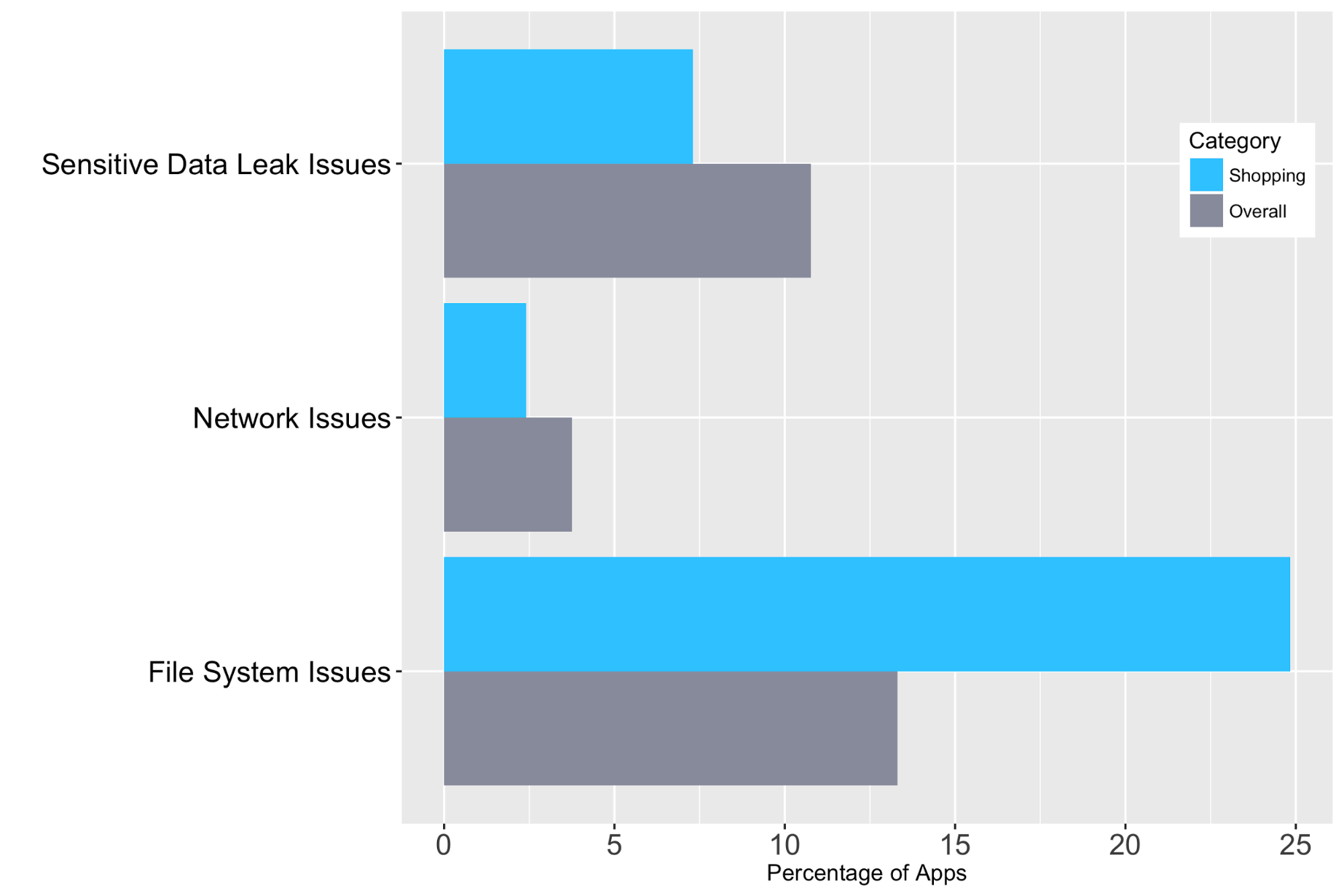
One in four apps exhibited a high-risk issue. Out of all the apps that were tested, a percentage of 13.3 was found to have file system issues. The number of sensitive data leak and network problems in all mobile apps was lower than other problems.
You have a brilliant app in hand, spick and span, ready to sail.
You’re confident about the app’s features and functionality. It will hit the market and attract users like a magnet.
This is the story of an app narrated by a developer. Most of it, as you’d notice, is from a future perspective. But the present of your application lies in the hands of the user. What if a user narrates this tale? Will it still have the great ending?
A person scrolls through an app store and finds this interesting app, downloads it and explores through. The app asks for security details for log-in. The user follows. A few hours later, he finds his device breached. Here comes ‘The End’! With no protection, the user suffers considerable damage, and so does your reputation.
If you don’t want your app to go down the same lane, read on!
Mobile apps are trending in the market. Almost every business, from sports to corporate industries, are looking to hop onto this trend. But with the growing field, risks have also proliferated beyond our reach. App malware and security breaches are almost as much in number as the apps. This parallel can be extended to their growth pace as well.
With mega attacks like Pegasus, mobile applications have become susceptible to threats never witnessed before. The Pegasus attack, for example, was one of the reasons app security has been brought up to the front.
The attack targeted iOS Spyware. Once inside your device, it could spy in almost every detail of the device from voice communications and contact list, to passwords, messages, GPS, etc. It’s not just breaching, but some of these even manage to scam through behaviour manipulation.
The problem with such security issues is that it is impossible to make an app 100% secure. On the other hand, user concerns over security can’t be ignored. So, we need to find a way to get into the mind of the hacker and block every path that hackers could take to get into the app.
Understanding the need of the hour, we have put in time and effort to give you a broader perspective of the situation.
400,000 apps were put to the test and following security risk, related data was collected and sort out based on app category.
Business Apps
Gaming Apps
Shopping Apps
To put an end to the problem we need to determine the nature of threats faced by mobile apps.
There are mainly four types of threats that can ruin your app and its reputation.
Privacy Threat
Mobile apps gather extensive information from the device, like contact list, online history, emails, location, etc. These apps may not necessarily intend to harm or scam the user. For example- the advertisements on free apps are managed according to the user’s preference. This preference is determined with the help of personal information that the mobile application collects from the device. Third-party involvement in the functioning of the application revenue system immediately puts the personal information of the user at risk.
Spyware
A spyware functions in a similar fashion. But unlike privacy threats, spyware accesses personal data without any warning and knowledge of the user. The Pegasus attack mentioned above is an example of spyware theft. During a Spyware attack, hackers can manage to access personal details through, contact list, location, call history, browser history, text messages, photos, and emails. This much information is enough to commit financial frauds or identity thefts.
Malware
It is a software that gets installed on the user’s device. Once installed, it initiates a disruption and gives attackers the control of your device. It could handle messages and charge bills without any knowledge or input of the user.
Last year, a malware attacked mobile banking apps of Australia’s big banks. Customers of National Australian Bank, Westpac, Commonwealth Bank and ANZ all were under threat. The malware apparently tricked the users into giving away their bank details and passwords. (Source)
Vulnerable Applications
Loosely encrypted apps expose the user’s device to significant vulnerabilities.
One of the most famous attacks that victimised thousands of Australian Government officials is the Yahoo Hack. The Yahoo data breach compromised email accounts of Australian politicians, police officials, and judges. About 3000 log-in credentials linked to private Yahoo services rooted to Australian Government email accounts were spilt. (Source)
Your mobile application can generate revenue only if it works to the benefit of the users. You need to fill these gaps before they begin to threaten the foundation of your app.
Here are 7 loose ends of application security that could pose a massive threat to your mobile app
1. Virtual Private Networks
Privacy risks, where information of the user becomes an easy target for hackers, and advertising agencies are a common concern today. Supported by such violation of privacy on moral grounds, identity theft and similar frauds have become fairly standard.
Avid Life Media (Now: Ruby Life) that has its headquarters in Canada and its website reaching millions including Australian users witnessed a breach by ‘The Impact Team’ in 2015. 36 million users found their information compromised.
Virtual Private Network supported app building is one of the ways you can ensure app security.
Through VPNs, apps that need internet access for functioning, work on encrypted data so that it can’t be deciphered by any third party. It secures the device’s internet connection. Therefore the user can access public internet services free from all kinds of cyber-threats. Australia has recently been depreciated as one of the most snooped on locations in the world.

In defence, Electronic Frontier’s Association in Australia has been encouraging privacy protected the access to internet service through VPN. Besides this, VPN protects from prying eyes of the government. To ensure that the users of your mobile application can avoid hackers without any hustle, you should be sure that the application you are building is friendly towards the use of Customer Virtual Private Network.
2. Log-In Credentials
Login credentials for your app should fall into properly encrypted security measures. Convert your code into indecipherable complex coding. Many apps store the username and password in clear text. This information means that your email address, password usernames, etc. are all at risk. Anyone can get access to all this data just by connecting your phone to the PC.
This issue may seem too simple and ignorant to be true. But leading branding have been known to fall into this pit. Starbucks, one of the most popular mobile payment apps in the US recently accepted that it stored its data in clear text.

With this kind of information out in the open, any unauthorised individuals can access login credentials to the Starbucks website as well.
Set up a two-factor authentication login requirement. After a user has entered the username and password, a third factor is asked. This third element could be either a mobile authentication, e-mail authentication, etc. Make this a standard level security, user-friendly, so that your app users don’t find it cumbersome.
Moreover, apps should be designed to protect critical information like password and credit card number by avoiding saving them directly to the device.
3. In-App Security
To avoid the cumbersome process of code encryption, developers often use ready-made codes to build their apps with minor alterations. Hackers place bugs in already created codes or even create codes to gain access to the application’s information after it ’s release. Popularly used algorithms like MD5 and SHA1 were found to hold insufficient security weight. A well-known gaming app Angry Birds was hacked, and the official Angry Birds graphic was replaced by Spying Birds logo. While the whole thing was restored in a matter of a few hours, this was a huge sign indicating the danger of leaky apps or lack of proper in-app security. This app, which gathers chunks of personal data like age, location, etc., from its customers was guilty of laying it all at risk.

Modern algorithms approved as reliable by the security community should be your highest priority. Usage of state-of-the-art encryption APIs should be promoted within mobile platforms. Active key management should be encouraged as poor key management may even put strongly encrypted apps at risk.
4. Unauthorised User Data Access
When applications use private and sensitive user information, they connect back to a server.
Authorisation of that server is necessary to protect the information, the user of your application has entrusted you with.
A mobile app called Path that offered an excellent way to socialise with friends was lauded for its brilliant UI design. But little did we know, that Path uploaded the entire contact list to its servers. It did not ask permission for this in its iOS version.
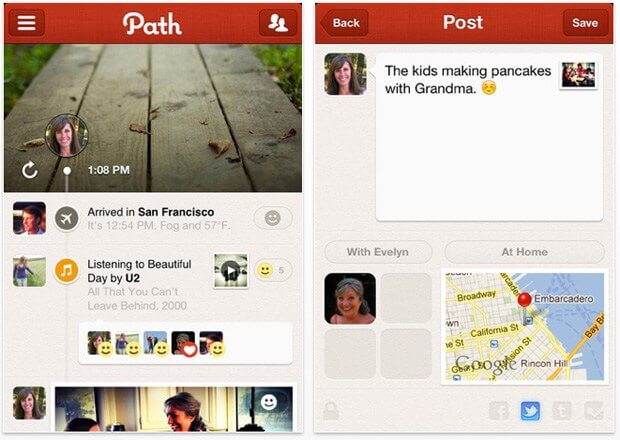
To secure communications to servers is needed keeping in mind that the user will also access public WiFi networks. Encryption, SSH keys and SSL certificates can ensure this authorised access. SSLs are Secure Sockets Layers. This security protocol provides secure channels between two machines. TLS i.e.; Transport Layer Security is a similar service that also enables security over the internet as well as an internal network. SSH is Secure Shell network protocol. It uses public key cryptography to authorise remote computer. SSH key approves even password authentication in an entirely encrypted manner. This encryption is an easy way to barricade any malice compromising user information.
5. User Privacy Security
In the absence of sufficient encryption, a mobile accepts data from all kinds of sources. Attackers can modify inputs and based on this bypass your app security. A similar flaw in Skype data security allowed hackers to dial arbitrary numbers with a simple link in your email.

Enterprise Mobility Management Solutions (EMM) is that additional step that’ll pay for various safety requirements. This can provide solutions, like security data transcription. Enterprise authentication requirements that developers usually miss out on can be solved by EMM solutions, to a large extent.
Before equipping your app with a personalised data security features, make sure your developers have thought about and made arrangements for such unintended consequences.
6. Simplicity
Simplicity should not mean that you should compromise on security. In fact, designing simple apps implies that it should be easier to go through the security procedures for the user. It is no way indicating that the developer is allowed to skip on the important safety features for user’s ease.

Under the ruse of providing easy logins, customers of popular apps just enter their password once when activating the payment portion of their app. In such a case, user data security should be maintained. If critical information like email and credit card details lie directly in the device, anyone can access the information by gaining access to the device. Data, Network, Device and Application are critical areas of concern in this respect.
7. Testing
Different devices have different capabilities, features and functions. Device fragmentation is a phenomenon due to which app testing needs to cover a large number of mobile device type. App development needs to keep up with app testing procedure.
Traditional testing tools like Selenium or QuickTest Professional (QTP) lack sensitivity to this multiplicity. Testing teams often fall short in their coverage and release apps with low-quality security.
Automation testing can be used to fill this gap between the development of an app, testing and release of an app. Automated testing it is efficient, cheap and reliable.
Mobile automation testing tools that can help solve this problem are Calabash, Frank, Appium, Robotium, and Ranorex.
While building an app make sure that your designer is aware of all these loopholes that could drown your app.
We at Enterprise Monkey go much beyond knicks and knacks to give you the best product you can have at your service.



 Source
Source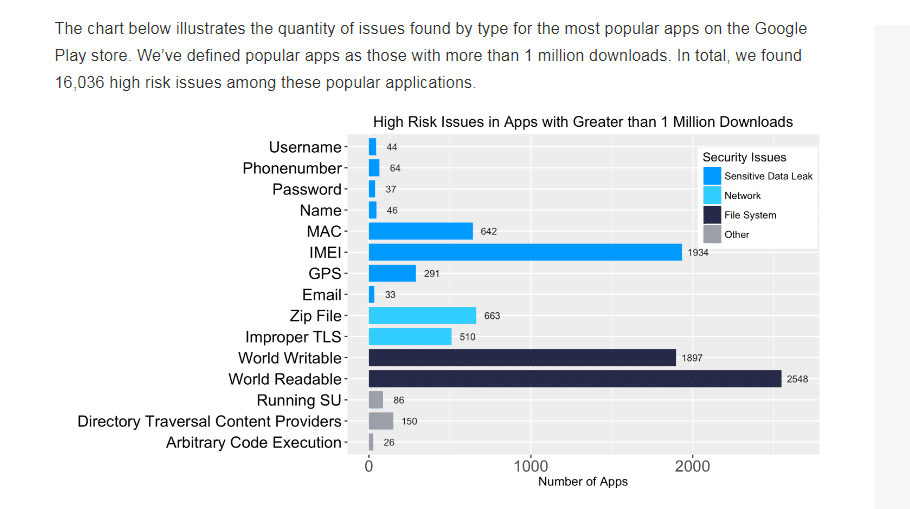 Source
Source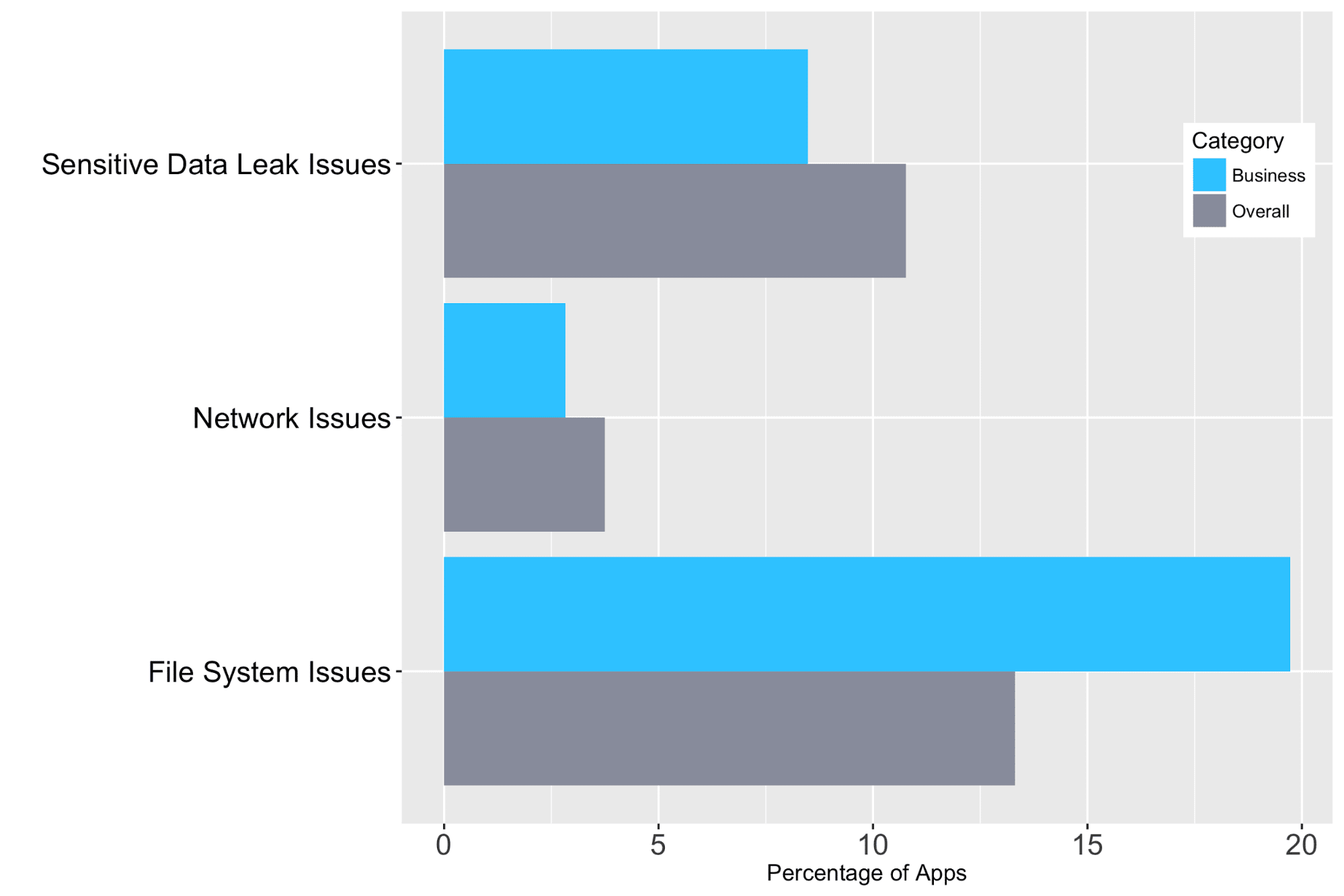 Source
Source






